Automated Threat Hunting At Scale
The Benefits and Challenges of Scaling Threat Hunting
Threats evolve on a continuous basis, as do the workloads and systems they penetrate. In the not-so-distant past, we relied on traditional antivirus and perimeter firewalls to defend us and that was “good enough”. Today, that is no longer works…
Threat Hunting “At Scale” is Required
YARA is today’s threat hunting standard in advanced, automated malware hunting languages. Without it, security pros would be triaging manually, downloading hash-sets, comparing files and investigating logs using a relatively low amount of detection detail. Yara scanning changes detection dynamics entirely. Without the advanced pattern matching and file content analysis capabilities in YARA, we would literally completely miss the many advanced threats that plague us constantly .
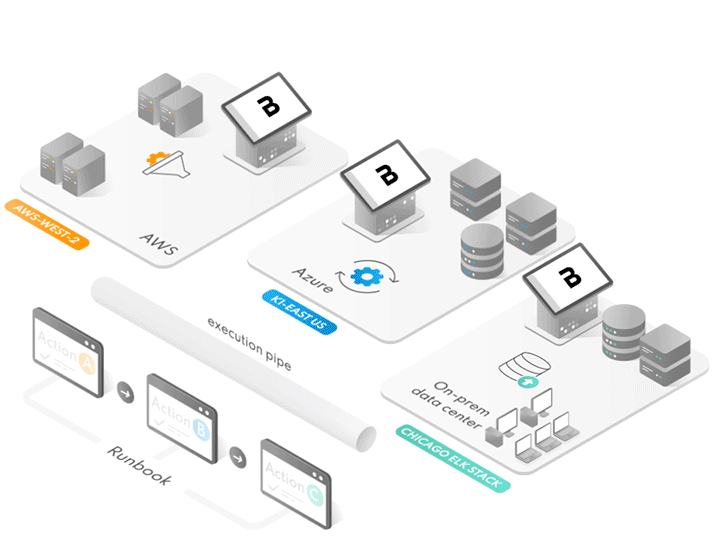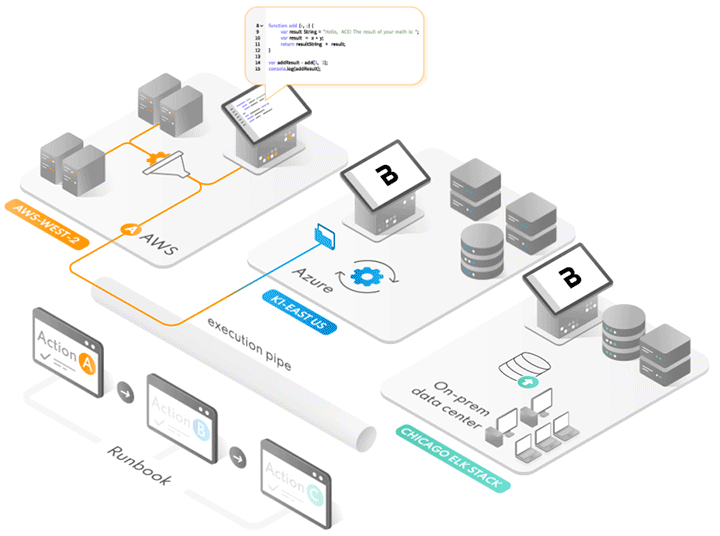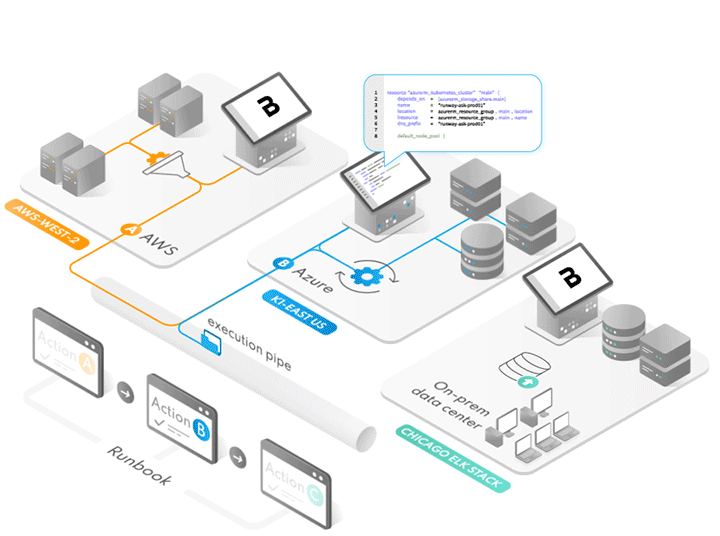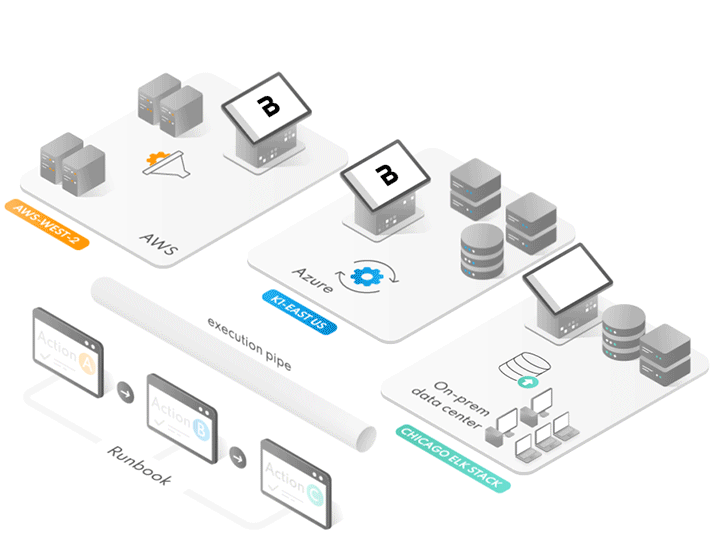
Unfortunately, the cloud and the adoption of multi-cloud is driving greater need for scaled hunt capabilities and enhancing our need for rapid hunt capabilities. Today, security operations organizations must be able to deliver greater performance and satisfaction with their limited threat hunter resources and security operations personnel, automating hunt and advanced detections tasks in order to deliver speed of incident response and rapidly scale to the workloads - wherever they may be.
Brazen Agent Operating Systems Supported
Windows
Linux
Workloads, Containers, Servers and Workstations
Learn more About BrazenCloud’s Features
Learn more about BrazenCloud’s Technology
BrazenCloud Saves Time for Threat Hunters and SecOps
Example: YARA Runbook Actions In BrazenCloud
Want to Yara Hunt at Scale? Seeing is Believing.
More BrazenCloud Use Cases
BrazenCloud
Hunt Everywhere: Fast
Rapidly Hunt your multi-cloud or
on-premises in minutes
Move the hunt wherever the threat goes
Execute Yara Rules and Threat hunting tools quickly
across all your workloadsScan your DMZ workloads without network changes
Built-In Out-of-the-Box Actions Supported (Examples):
Yara Rule Scanning at Scale
Cobaltstrike beacon scans on all Windows hosts
Process Scanning with Loki for Advanced in-Memory Malware
Rootkit Scanning with rkhunter, chkrootkit and PESieve Across Linux and Windows Hosts
Instantly install Nmap on a Linux workload and launch a scan from it (External or Internal Attack Surface assessment)
Do deep on-demand analysis of files with radare2 instantly to any file on Windows. Delivers Executable analysis: Hashing, pe file headers, imported and exported executable functions detail with strings output.