Security Automation for Managed Service Providers
Built on a Zero Trust Data Fabric
XDR/MDR Response Automation
Deliver straight-line, pre-scripted response automations without the overhead of SOAR. Get more out of SIEM by adding automated response. Use triggers to enrich events and perform automated hunts over live endpoints.
Script, Set, and Forget
Brazencloud contains hundreds of out-of-the-box automations. Check out the open-source repository developed by the community.
Power users can create bespoke actions using powershell or python. Click here for more information on the Powershell SDK and Python SDK.
Be Prepared, Get There Fast
Immediate recovery, remediation, and deployment capability
Eliminate the cost of dwell time and improve the mean time to response
Proactive, continuous mapping of the ever-changing environment
Response Readiness begins by knowing which assets are in the environment. Continuous asset discovery is fundamental to ensure security coverage. Every day the environment changes. Having an up-to-date view of the ever-changing environment reduces critical dwell-time in the beginning of an engagement.
Incident responders no longer have to spend days or weeks mapping the environment and deploying agents to begin a threat hunt or remediation.
Brazencloud has built-in, network-native asset discovery that doesn’t depend on external API connections. BrazenCloud is capable over hybrid, on-prem, and multi-cloud. Brazencloud gives responders the tools they need to begin working in the environment immediately.
See what you are missing.
Live Threat Hunting
Don’t rely on sampling of results. Go beyond the data lake or log files. Get ground-truth results from live endpoints.
Use multi-stage runbooks to evaluate the hypothesis and iterate the results of the threat hunt across multiple disparate systems in the Enterprise.
Brazencloud supports best-of-breed tools like sysmon, osquery, sigma rules, and yara signatures.
Operationalize Investigations
Scales Up to any number of Workloads Enterprise-Wide
Deliver rich telemetry from Endpoints to Analytics tools
Deploy and Execute Runbooks Anywhere either Multi-cloud or On Premise
Inject Applications into Kubernetes Pods (pre or post CI/CD)
Operating Systems Supported
Windows
Linux
Workloads, Containers, Servers and Workstations
BrazenCloud provides a unified console to deploy and manage Enterprise agents and tools, and orchestrate the dataflow between components.
Save Time. Improve Mean Time to Response. Fast and automated deployment of 3rd party agents and open-source tools
Managed deployment of agents like CarbonBlack, Guardicore, CrowdStrike, Sentinel One, Velociraptor, etc.
Improve security readiness. Asset discovery is baked into the solution so there are no gaps in visibility. With BrazenCloud you can measure estate coverage.
Network discovery using all the industry techniques like TTL controlled scans, SSDP, ICMP, DNS and ARP cache, Hardware fingerprinting
Frictionless and Open. Leverage open scripting languages and tools you know and love, such as PowerShell and Python. This is a low code approach to script nearly any bespoke action at the endpoint.
You can deploy any executable or script to an endpoint. BrazenCloud includes a position-independent python exe so you don’t need python to be installed ahead of time.
For power users, BrazenCloud can do nearly anything at an endpoint, not just security use cases
Operationalize hundreds of trusted free and open source tools at Enterprise scale.
Threat hunt with tools like osquery or yara
Stream telemetry with tools like sysmon or tshark. Because BrazenCloud has a native data fabric, data can be streamed to any ETL point anywhere on the planet with zero configuration changes to the customer network.
Snapshot memory or disk at scale with readily available forensic tools like winpmem, volatility, and raw NTFS disk imaging
Connect and integrate with nearly anything. Everything in BrazenCloud is defined as a data pipeline with as many inputs, outputs, and processing points you wish.
Snapshot and store data on a trusted S3 container
Stream telemetry to Elastic or Splunk
Process and filter data in transit to increase fidelity and save cost
Simplified Automations
Example Automation: Create a Certificate Signing Request, Sign a Certificate, and then push certificates to all nodes in only a few clicks.
Want to Consolidate Your Automation?
What are Runbooks?
Easy to use Automations - Pipelines are sets of actions to deploy and execute Security, IT and DevOps tasks on workloads or endpoints.
Leverage Pre-Defined Pipelines - Simply select the Pipeline and assets you wish to automate against, define desired actions and the BrazenCloud automation framework handles the rest.
Crowdsourced Actions - Runbook actions are shared and crowdsourced by both BrazenCloud staff and our user community via the BrazenCloud Pubic GitHub Action repository. Private repositories of actions are also supported.
Composable - BrazenCloud clients can create tailored Pipeline compositions to carry out countless tasks which otherwise requires manual human intervention or multiple administrative consoles.
Limitless Pipeline Action Combinations are Possible - Fully customizable execution steps and stages include variable passing, full cli parameter’s passed to executables, and customizable variables for actions exposed easily for admins in the BrazenCloud UI.
Power Users and Security Pros - Build bespoke automations and integrations using the BrazenCloud REST API and SDKs for PowerShell and Python.
Stay Frosty
Articles & Insights
Leadership ❯❯
Greg Hoglund
❯❯ Founder
Greg has a highly successful track record with software startups having been CEO and Founder of Cenzic, HBGary, and Outlier Security. Greg contributed early research on rootkits, software exploitation, buffer overflows, and online game hacking. His later work focused on computer forensics, incident response, physical memory forensics, malware detection, and attribution of hackers. He authored three security books including Rootkits: Subverting the Windows Kernel, Exploiting Software: How to Break Code, and Exploiting Online Games: Cheating Massively Distributed Systems.


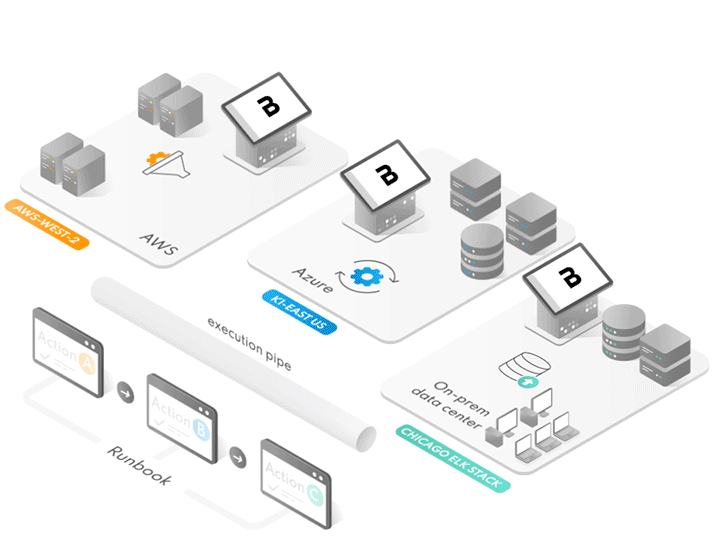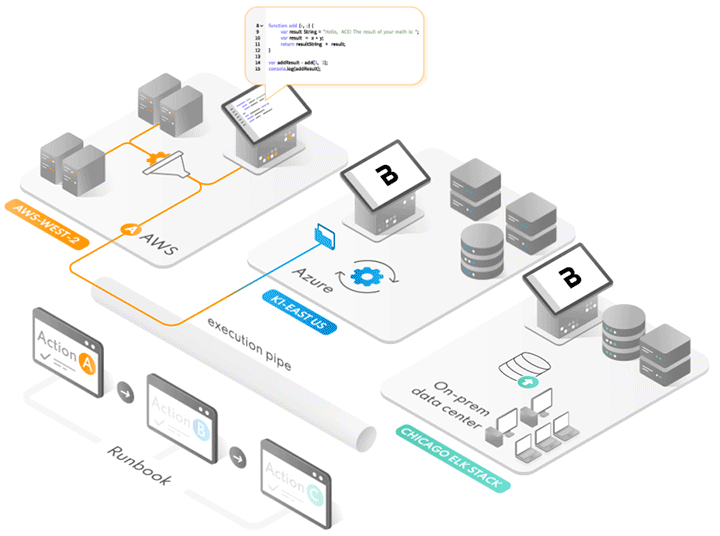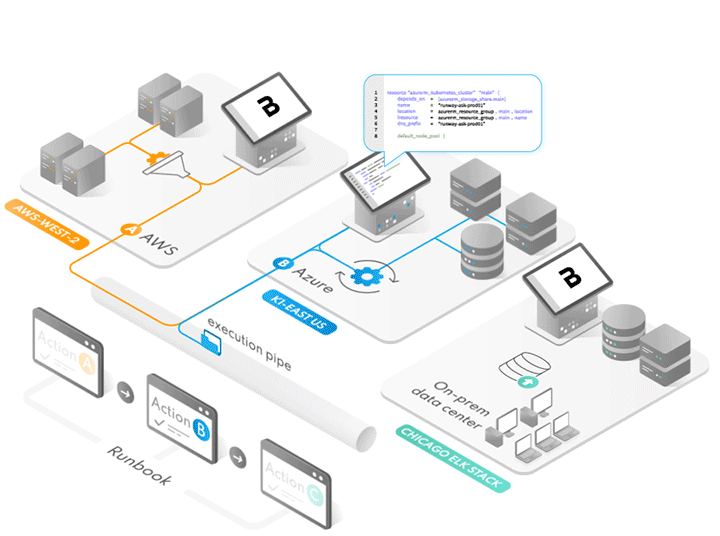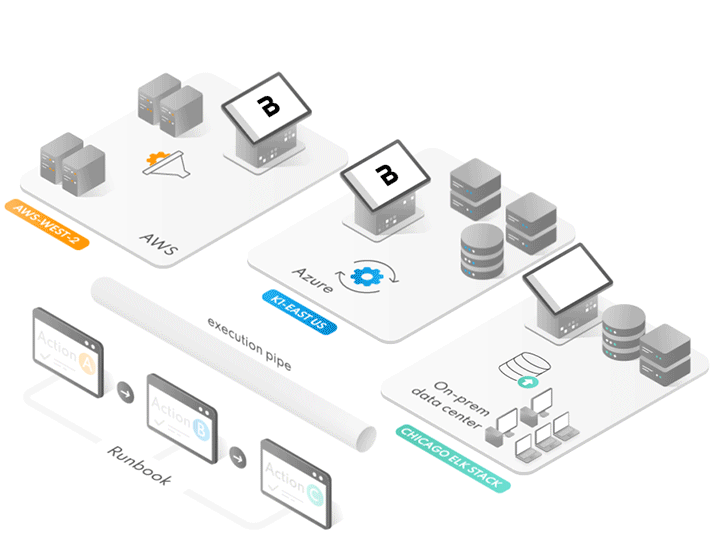
















Sick of complex networking requirements and managing VPNs just to get some data between two endpoints with no pre-existing connection? Then maybe you should check out Runway…